VMware in Linux : The virtual machine's operating system has attempted to enable promiscuous mode on adapter Ethernet0
I was just happy when I transported my dev virtual box to my Linux system. But immediately after starting up the system I was greeted with this error
Apparently the solution is this.
Which states that "VMware software does not allow the virtual Ethernet adapter to go into promiscuous mode unless the user running the VMware software has permission to make that setting. This follows the standard Linux practice that only root can put a network interface into promiscuous mode."
And the solution it seems is adding a new user group and deligating permission to them. However for CentOS this didn't turn out to be the case. Apparently device nodes are created in boottime in this case and you need ownership permissions for udev to make it work.
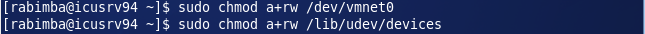
You can read a detailed description in that link. But in short the commands which will solve your problem (and conveniently absent in the help article) are
cp -rp /dev/vmnet0 /lib/udev/devices/
sudo chmod a+rw /dev/vmnet0
sudo chmod a+rw /lib/udev/devices
The virtual machine's operating system has attempted to enable promiscuous mode on adapter Ethernet0. This is not allowed for security reasons.
Apparently the solution is this.
Which states that "VMware software does not allow the virtual Ethernet adapter to go into promiscuous mode unless the user running the VMware software has permission to make that setting. This follows the standard Linux practice that only root can put a network interface into promiscuous mode."
And the solution it seems is adding a new user group and deligating permission to them. However for CentOS this didn't turn out to be the case. Apparently device nodes are created in boottime in this case and you need ownership permissions for udev to make it work.
You can read a detailed description in that link. But in short the commands which will solve your problem (and conveniently absent in the help article) are
cp -rp /dev/vmnet0 /lib/udev/devices/
sudo chmod a+rw /dev/vmnet0
sudo chmod a+rw /lib/udev/devices
As you can see here

Comments
Post a Comment